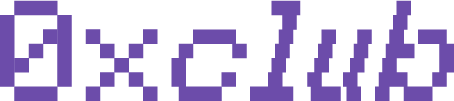
Bedu: Streamlined Operations
Bedu is an innovative booking platform tailored for travelers seeking unforgettable experiences in the MENA region with destinations ranging across the UAE, Lebanon, and Saudi Arabia. Their user-friendly website serves as a comprehensive guide, showcasing entertainment and culinary hot-spots across these three countries. They enable users to plan and personalize their trips, providing a journey through the region’s cultural and culinary richness. With Bedu, users can effortlessly schedule reservations at their preferred establishments, ensuring a hassle-free and enjoyable travel experience.